6 Key Questions to Ask About Secure QR Codes for Document Security
- Rajesh Soundararajan
- Jun 14, 2022
- 2 min read
Discover the Difference: Secure QR Codes Explained
Document security has come a long way from what it was a decade ago. Today, we have access to robust and easy-to-deploy solutions featuring highly compressed, digitally signed QR codes that enable on-demand, decentralized validation. Secure QR codes have revolutionized the way businesses handle document security.
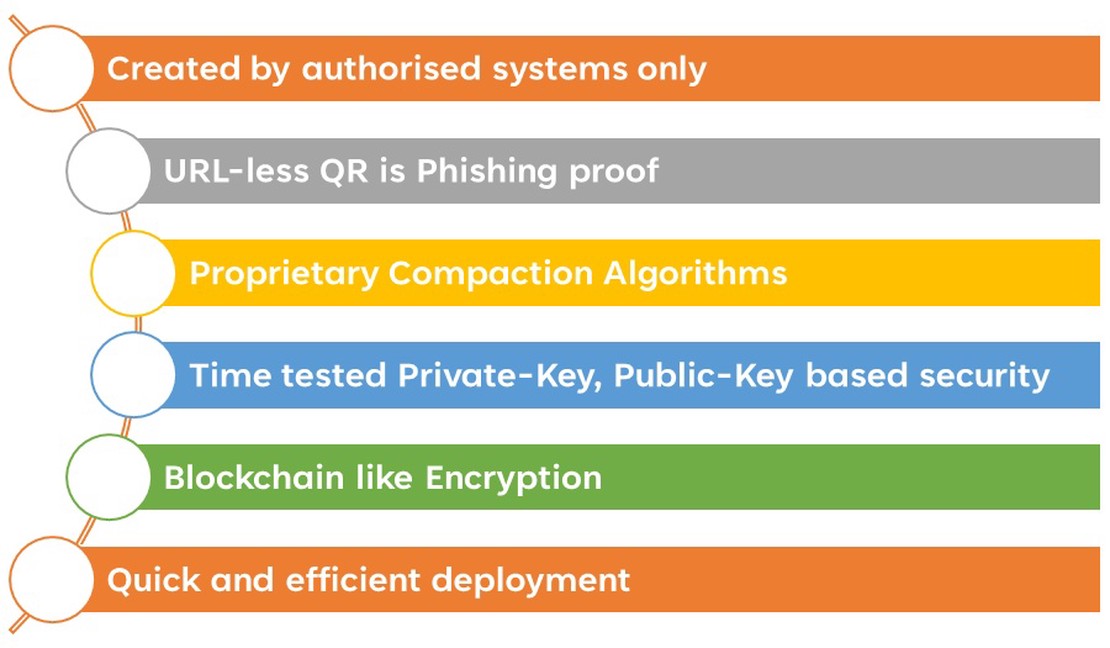
Here are six key differences between secure and regular QR codes:
1. Created by authorized systems only
Secure QR codes are digitally signed by the issuer’s private key and can only be created by their authorized systems/personnel. This prevents tampering and unauthorized modification. In contrast, regular QR codes lack security and can be created or altered by anyone, making them unsuitable for most document security needs.
2. URL-less QR is phishing-proof
Regular QR codes often contain URLs, making them vulnerable to phishing attacks. Ideally, QR codes should not include URLs. However, a secure QR code can support this option when necessary.
3. Time-tested Private-Key, Public-Key based security (PKI)
Secure QR codes are signed with a private key, meaning they can only be read by an app, QR reader, or validation mechanism with the corresponding public key. This enhances security and privacy. Regular QR codes, on the other hand, can be scanned by any generic QR reader, potentially exposing sensitive personal data.
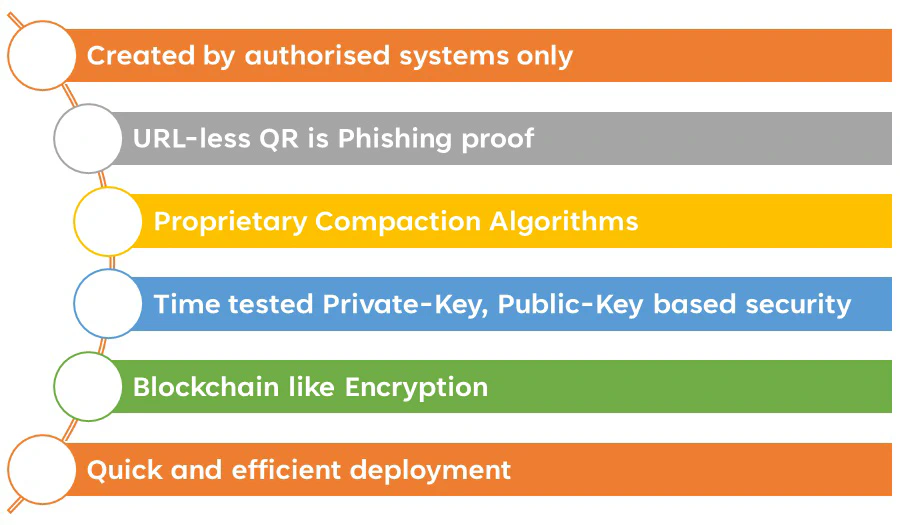
4. Proprietary Compaction Algorithms
Using proprietary algorithms to generate compact, secure QR codes with high levels of information integrity is advantageous. This approach creates smaller, more secure QR codes for a given amount of information. Qryptal, for example, employs such an algorithm.
5. Blockchain-like Encryption
Secure QR technology combines QR codes with blockchain-like encryption and digital signing, enabling centralized “truth” generation and decentralized validation in a scalable, cost-effective manner. This approach has been proven successful in numerous use cases.
6. Quick and efficient deployment
Although QR codes are based on open standards, companies like Qryptal have developed secure solutions that prioritize ease of use. Standard-based architecture and microservices enable rapid, successful deployments within days.
Qryptal’s QR code solution encompasses all of the above features. With their technical expertise, Qryptal can help you implement this technology efficiently and successfully, adapting to any changes in specifications or requirements over time. They can also deploy the solution at scale to handle millions of codes for various use cases.
You may also like
- A Definitive Guide to Using QR Codes
- Why your QR Code document strategy cannot be an after-thought
- Top 10 searched terms in QR Codes in 2021 - Qryptal
- QR Phishing: Stop placing URLs in QR Codes when security and privacy is paramount